PREVIOUS
Computer Technology - Terms & Definitions
December 23 , 2017
2678 days
4522
0
Computer Technology - Terms & Definitions
A collection of Important terminologies which are in recent news
- - - - - - - - - - - - -
1. BIG DATA
- Big data is the term for a collection of data sets so large and complex that it becomes difficult to process using on-hand database management tools or traditional data processing applications.
- It exceeds the processing ability of conventional data systems and requires us to use an alternate way to process it so as to gain value from the data.
- Challenges include capture, storage, analysis, data curation, search, sharing, transfer, visualization, querying, updating and information privacy.
- The data could be from social networks, web server logs, traffic flow sensors, satellite imagery, broadcast audio streams, banking transactions, music audio tracks, the content of web pages, scans of government documents, GPS trails, telemetry from automobiles, financial market data and so on.
- It answers specific questions such as the need of the customers, their opinion and image of the brand
- For the first time the recent Economic Survey of 2016-2017 has used Big Data Analysis to shed new light on.
2. ARTIFICIAL INTELLIGENCE
- AI or artificial intelligence is the simulation of human intelligence processes by machines, especially computer systems. Simply AI is an intelligence exhibited by machines.
Description:
- The term was coined in 1956 by John McCarthy at the Massachusetts Institute of Technology.
- These processes include learning (the acquisition of information and rules for using the information), reasoning (using the rules to reach approximate or definite conclusions), and self-correction.
- Particular applications of AI include expert systems, speech recognition and machine vision.

- AI is becoming prevalent in all the sectors say, Health care, Education, Business, Space technology, Manufacturing etc.,
.
3. NEURAL NETWORK
- A neural network is a series of algorithms that attempts to identify underlying relationships in a set of data by using a process that mimics the way the human brain operates.
Description:
- Neural networks have the ability to adapt to changing input so the network produces the best possible result without the need to redesign the output criteria.
- A neural network operates similar to the brain’s neural network. A “neuron” in a neural network is a simple mathematical function capturing and organizing information according to an architecture.
- This is also known as Artificial neural networks.(ANN).
4. QR CODE
- QR Code (Quick Response Code) is a 2D matrix code that contains information on a specific task.
Description:
- QR code is first designed for the automotive industry in Japan.
- A barcode is a machine-readable optical label that contains information about the item to which it is attached.


- A QR code uses four standardized encoding modes (numeric, alphanumeric, byte/binary, and kanji) to efficiently store data.
- Recently Bharat QR code is launched for Digital payment.
- Bharat QR code is developed jointly by the four prominent card payment companies Master Card, American Express, Visa and NPCI (National Payment Corporation Of India) which run RuPay cards.
.
5. INTERNET OF THINGS
- The Internet of Things (IoT) is the network of physical objects—devices, vehicles, buildings and other items—embedded with electronics, software, sensors, and network connectivity that enables these objects to collect and exchange data.
Description:
- It is a kind of Machine to Machine communication which takes place via Internet by without having the presence of human beings.
- Data Transmission is done either in a wired mode or in wireless mode.
- It finds its wide range of application in house automation, smart cities, Industrial manufacturing, Healthcare systems and Automotive.
.
6. VIRTUAL REALITY
- Virtual reality (or VR) is a computer technology that uses software-generated images, sounds and other sensations to replicate a real environment.
Description:
- A person using virtual reality equipment is typically able to look around the artificial world, move about in it and interact with features or items that are depicted.
- Virtual realities artificially create sensory experiences, which can include sight, touch, hearing, and, less commonly, smell.

- VR supports the concept that if people fully immerse themselves in highly visual world which they explore by their own senses then this form of interaction can result in a new form of communication and understanding. VR is an outcome of past desires of humans to go beyond their real world by embracing cyberspace.
- Application of VR:HEALTHCARE:Psychological therapy – treating patients in a safe zone where they can experience situations they fear and get over it.
- Memory therapy, implant and surgical training to surgeons, speech training and personality development in people who are crowd phobic.
.
7. AUGMENTED REALITY
Definition:
- Augmented reality (or Merged reality) is the integration of digital information with the user’s environment in real time.
- Unlike virtual reality, which creates a totally artificial environment, augmented reality uses the existing environment and overlays new information on top of it.
Description:
- 3D = You can only see a 3D world = Sharukh Khan appears as if he is standing in front of you.
- Virtual Reality = You can feel a 3D world = You can talk and dance with Sharuk Khan.
- Merged Reality = You can combine real and fake 3D worlds = You can bring Sharukh Khan (virtual) to your room (real). Example: Navigation - Enhanced GPS systems are using augmented reality to make it easier to get from point A to point B using the phone’s camera in combination with the GPS, the users see the selected route over the live view of what is in front of the car. Here vitality is merged with real time movement of the car.


- The classic examples were Pokémon Go, HoloLens of Microsoft City lens of Nokia and ISRO’s SAKAAR application.
8. CLOUD COMPUTING
- Cloud computing, often referred to as simply “the cloud,” is the delivery of on-demand computing resources/services—everything from applications to data centers—over the internet.
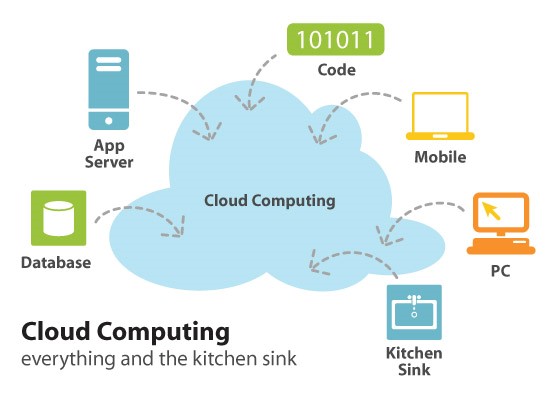
Description:
- Based on different computing resources, services include
| Type | Purpose | Provider(Ex) |
| Infrastructure as a service (IaaS) | Entire systems (virtual machines) will be provided to the users. Users can access the systems based on the resource allocated by Internet Service Provider. | Amazon |
| Platform as a service (PaaS) | In this model entire system along with the operating systems, software is provided. | Google App Engine |
| Software as a service (SaaS) | This one is more common Software created by service provider. End users use these services on a subscription basis | Yahoo, Gmail |
| Storage as a service (STaaS) | Storage is provided getting rid of maintaining separate storage devices. | Windows Sky Drive |
.
9. MALWARE
- It is a kind of software specially designed for breaching the data without the consent of the authorized user.
|
Examples of Malware (Malicious+Software) |
|
| Virus | A program which copies itself and multiplies |
| Worms | Copies and distributes itself through networks |
| Trojan | Seems like performing some function, but breaches security |
| Spyware | Covertly tracks your activities |
| Spam | Useless messages spreading through internet/emails |
| Phishing | Inducing you to reveal your passwords/bank details. E.g. those messages which claim that you have won a lottery. |
.
10. RANSOMWARE
- It is a type of malicious software designed to block access to a computer system until a sum of money is paid.
Description:
- Ransomware is a subset of malware
- All ransomeware are malware but all malwares are not ransomewares.
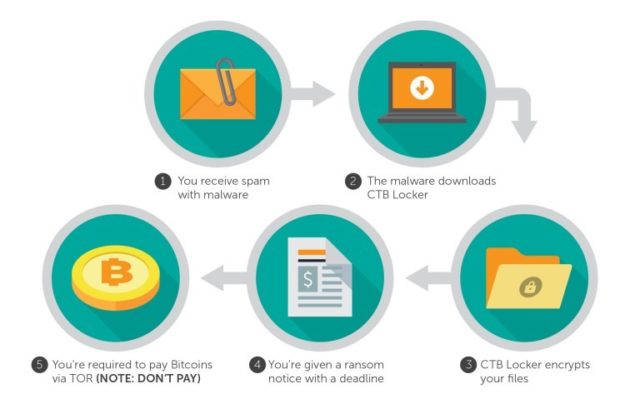
- The intrusion was a phishing attack, persuading a user to open a mail sent by a motivated intruder, appears to be from a genuine and authorized source, and the result of a malware (WannaCrypt 2.0) assembled not at one place but in several centers across the globe.
.
---------------
Leave a Reply
Your Comment is awaiting moderation.